How to enable sensitivity labels for containers
Author:
Vlastimil Sopuch
Published: February 7, 2022
4 minutes to read
In this day and age, users have to collaborate with others both inside and outside the organisation to achieve their daily tasks. This can present challenges around privacy, access and external sharing as the content no longer stays on the local network, and is likely being shared with guests. When this happens, you want it to do so in a secure, protected way that is within your organisation’s risk appetite.
Microsoft Information Protection (MIP) framework let you discover, classify, protect and monitor your organisation’s data across all endpoints, applications and services using predefined sensitivity labels, while making sure that user productivity and their ability to collaborate isn’t hindered.
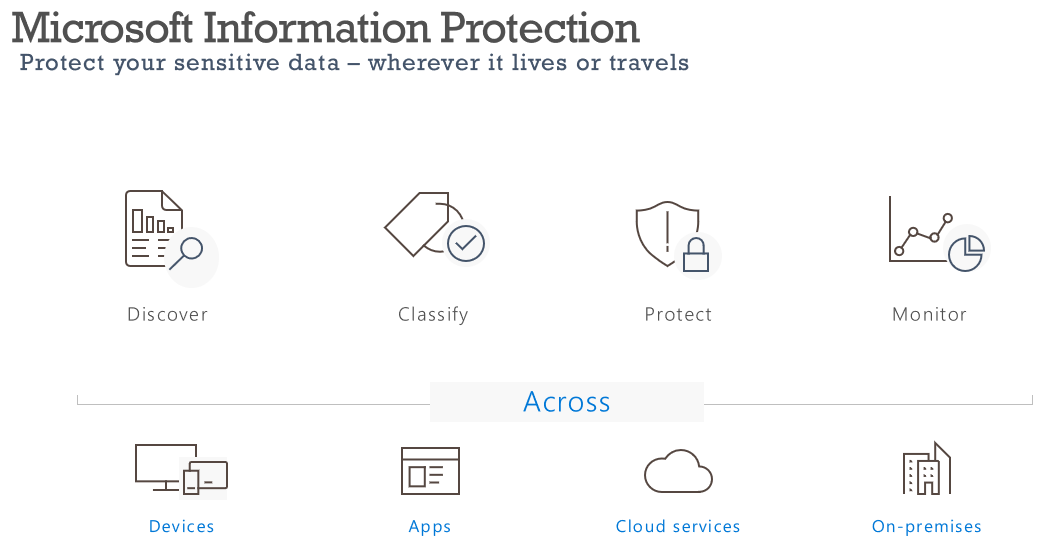
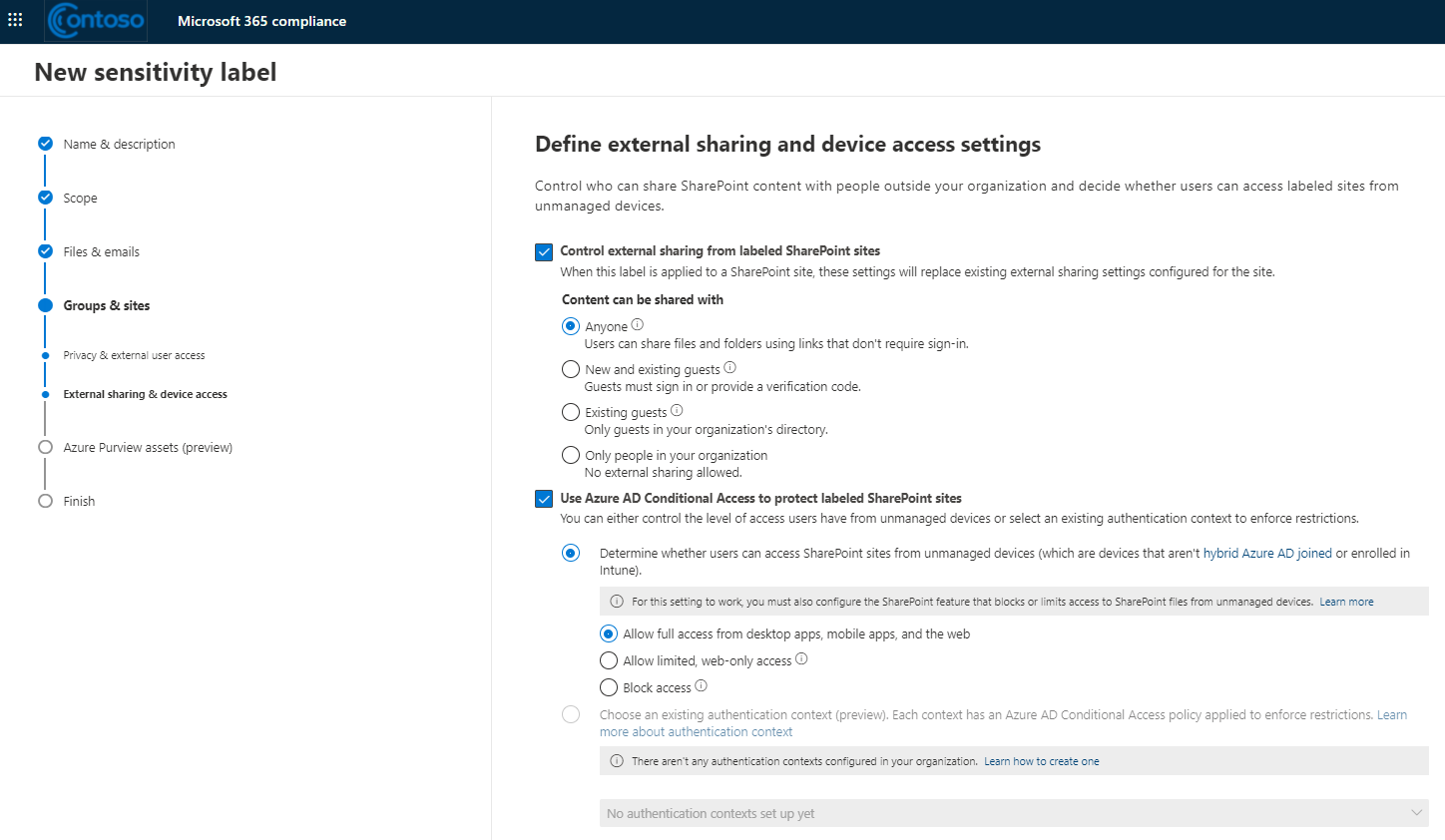
Most organisations are familiarized with sensitivity labels being applied across documents and emails, however their functionality can also be extended for container-level classification and protection. A container is your typical Microsoft Teams site, Microsoft 365 group or SharePoint site.
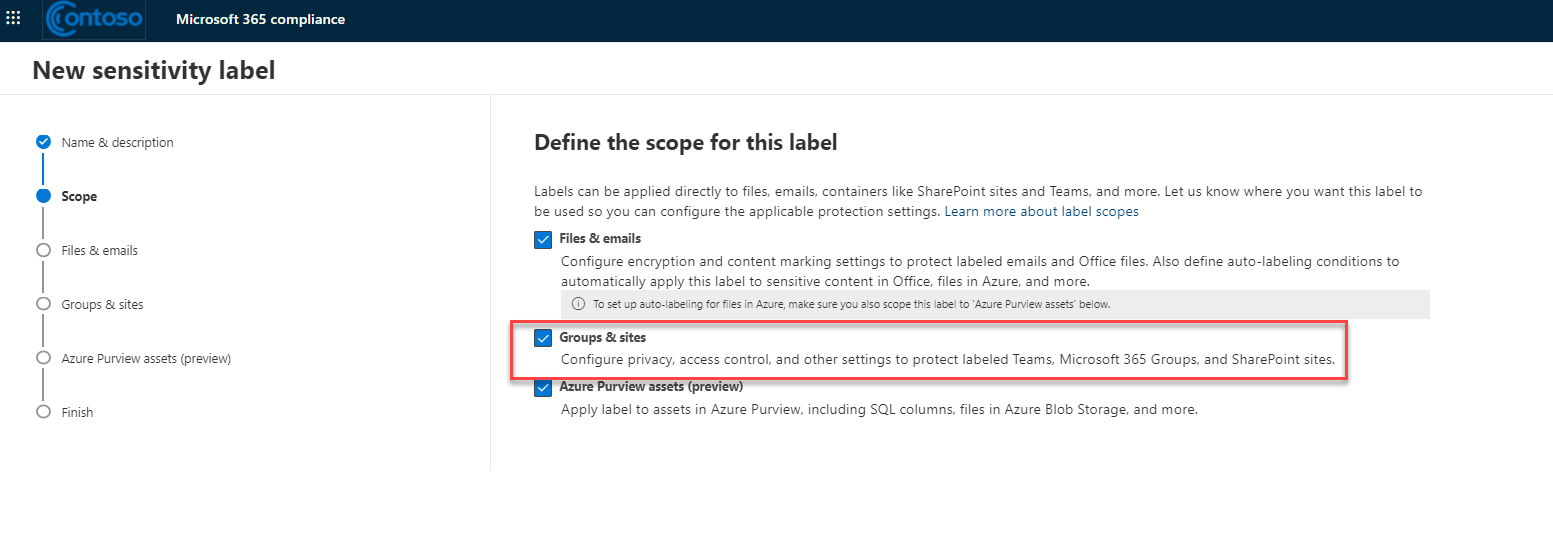
By enabling this feature in your Azure AD organisation, the following label configuration will be available to you:
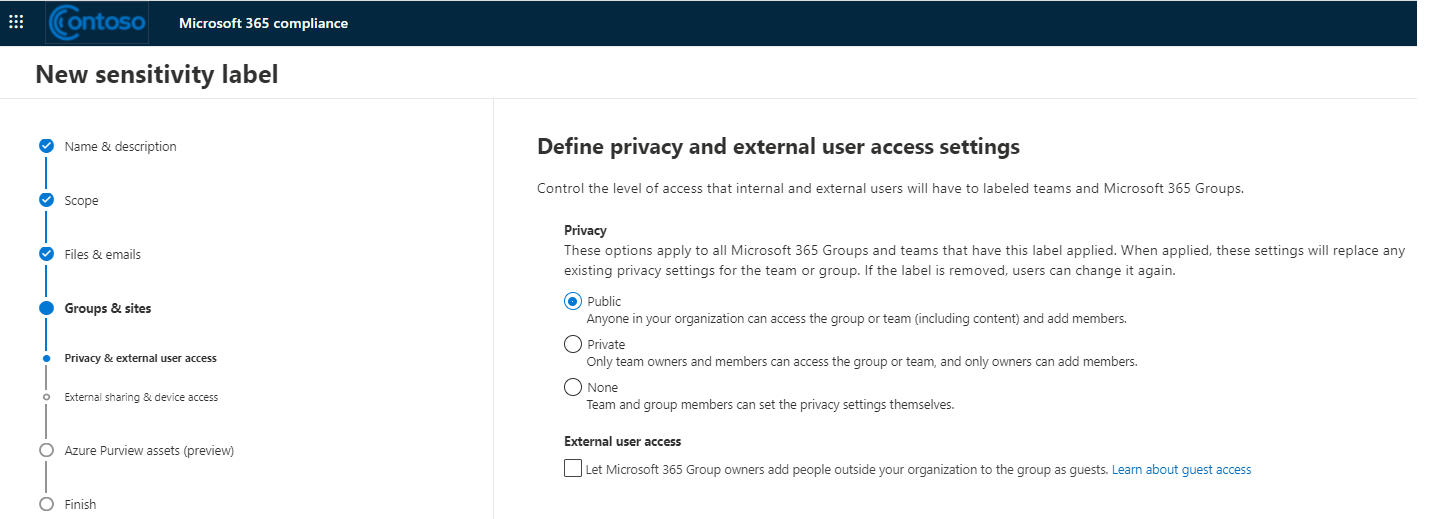
- Privacy (public or private) of teams sites and Microsoft 365 groups
- External user access
- External sharing from SharePoint sites
- Access from unmanaged devices
- Authentication contexts (in preview)
- Default sharing link for a SharePoint site (PowerShell-only configuration)
This will not only enrich the MIP reporting capability, but more importantly adjust the relevant tenant setting, allowing for more granular control. The content in these containers however, won’t inherit the labels for the classification or settings for emails and documents, such as visual markings and encryption.
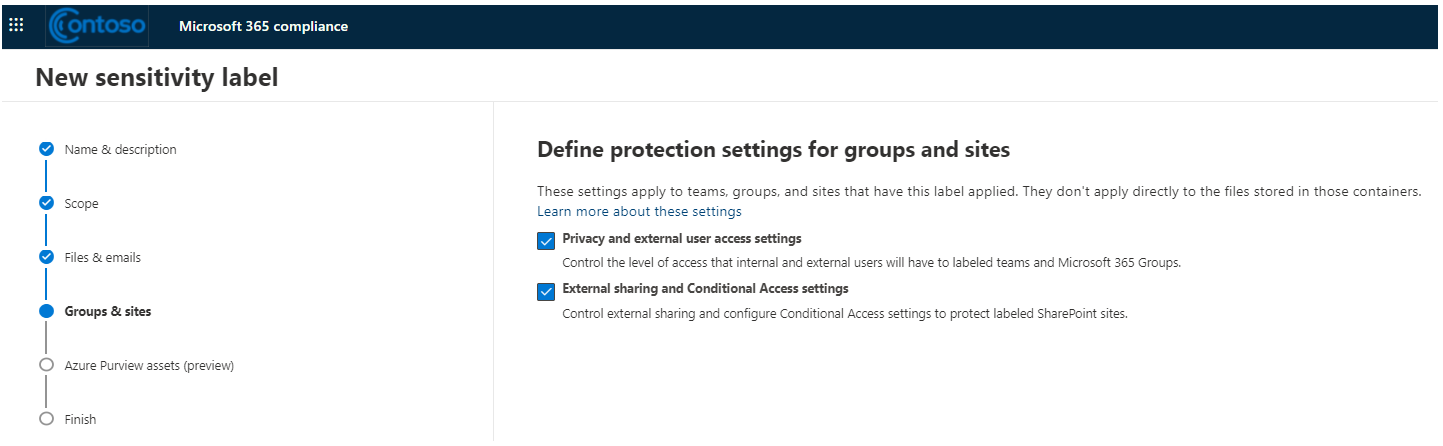
To configure the sensitivity labelling for containers, the following prerequisites must be met:
- Active Azure Active Directory Premium P1 licensing
- Global administrator role to run the below PowerShell
#Enable sensitivity label support
Install-Module AzureADPreview
Import-Module AzureADPreview
Connect-AzureAD
#Fetch the current group settings for the Azure AD organisation
$setting = (Get-AzureADDirectorySetting | where -Property DisplayName -Value "Group.Unified" -EQ)
$template = Get-AzureADDirectorySettingTemplate -Id 62375ab9-6b52-47ed-826b-58e47e0e304b
$setting = $template.CreateDirectorySetting()
#Enable the feature
$Setting["EnableMIPLabels"] = "True"
#Check the new applied value
$Setting.Values

#Create settings at the directory level
New-AzureADDirectorySetting -DirectorySetting $Setting
$Setting.Values
$Setting = Get-AzureADDirectorySetting | ? { $_.DisplayName -eq "Group.Unified"}
Set-AzureADDirectorySetting -Id $Setting.Id -DirectorySetting $Setting
#Enable sensitivity labels for containers and synchronize labels
Install-Module ExchangeOnlineManagement
Connect-IPPSSession -UserPrincipalName
Execute-AzureAdLabelSync
Conclusion
Microsoft Information Protection is a powerful framework that is always evolving to reflect your organisation’s needs around classification and protection of sensitive data, created and shared by your users daily. To help with the underlying privacy, external user access and sharing challenges, one can enable sensitivity labelling for containers (Groups & sites). When such label is applied to a supported container, the label automatically applies the classification and protection settings to the site or group and adjusts the relevant tenant setting, allowing for more granular control. Microsoft provides detailed information on how to enable sensitivity labels for containers via PowerShell which I have used to help guide this article.