Creating an Azure Landing Zone using Bicep - Part 2
 Stephen Tulp
Stephen Tulp
December 18, 2023
7 minutes to read

Introduction
In Part 1 of the series, we looked at the basics of what an Azure Landing Zone is and dissected the Bicep template to understand the different resources that that will be deployed as part of the Landing Zone. In this post, we will deploy an Azure Landing Zone using Bicep, both locally and using GitHub Actions.
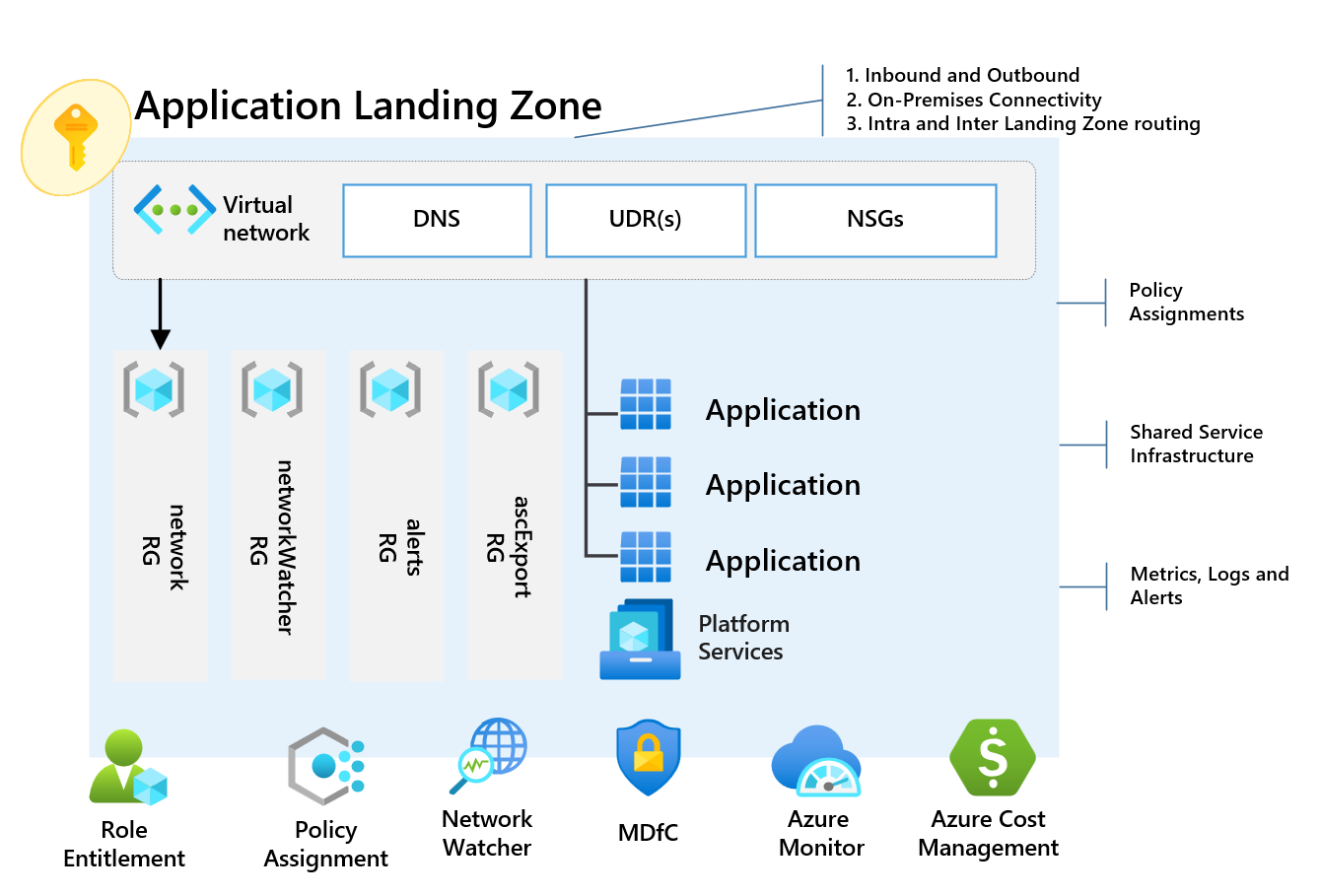
The diagram below outlines the architecture and what will be deployed to support applications and workloads, this will include all platform services that are inherited from the Management Group, including Role Based Access Control (RBAC), Azure Policy, Azure Monitor, Azure Security Center and Azure Cost Management.
Local Deployment using PowerShell
To get the Landing Zone deployment going locally, we are going to need 3 files
- The
Main.bicepBicep template, the has the Bicep code and referenced modules. - The
sub-sap-prd-01.parameters.bicepparamBicep parameters file with the parameters for the deployment. - The
landingZone.ps1PowerShell script that will deploy the above 2 files.
These files can be found in the Insight Bicep Advent Calendar Repo
The PowerShell script takes a couple of parameters for the deploymenName, location, managementGroupId, templateFile and templateParameterFile and will use the New-AzManagementGroupDeployment cmdlet to a Management scoped deployment into Azure.
$DeploymentName = ('lzVending' + ((Get-Date).ToUniversalTime()).ToString('MMdd-HHmm'))
$Location = 'australiaeast'
$ManagementGroupId = 'mg-alz'
$TemplateFile = '..\orchestration\main.bicep'
$TemplateParameterFile = '..\configuration\sub-sap-prd-01.parameters.bicepparam'
New-AzManagementGroupDeployment `
-Name $DeploymentName `
-TemplateFile $TemplateFile `
-TemplateParameterFile $TemplateParameterFile `
-Location $Location `
-ManagementGroupId $ManagementGroupId `
-Verbose
If you want to see what will be deployed first, you can change the -Verbose to -WhatIf and it will show you the changes that will be made.
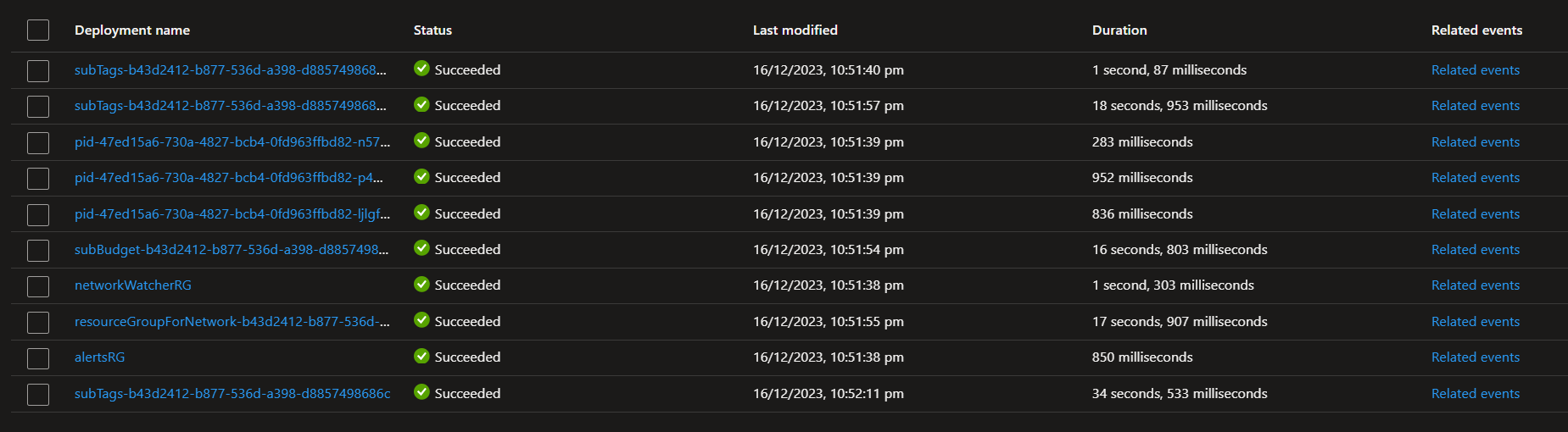
If we look at the deployment in the Azure Portal, we can see that the deployment across the subscription and resource group has been successful.
Subscription Deployment
The subscription deployment will create the resource groups and assign the tags to the subscription and resource groups. It will also create the Azure Budget and assign the Microsoft Entra security group to the subscription with Reader access and the Service Principal with Owner access.
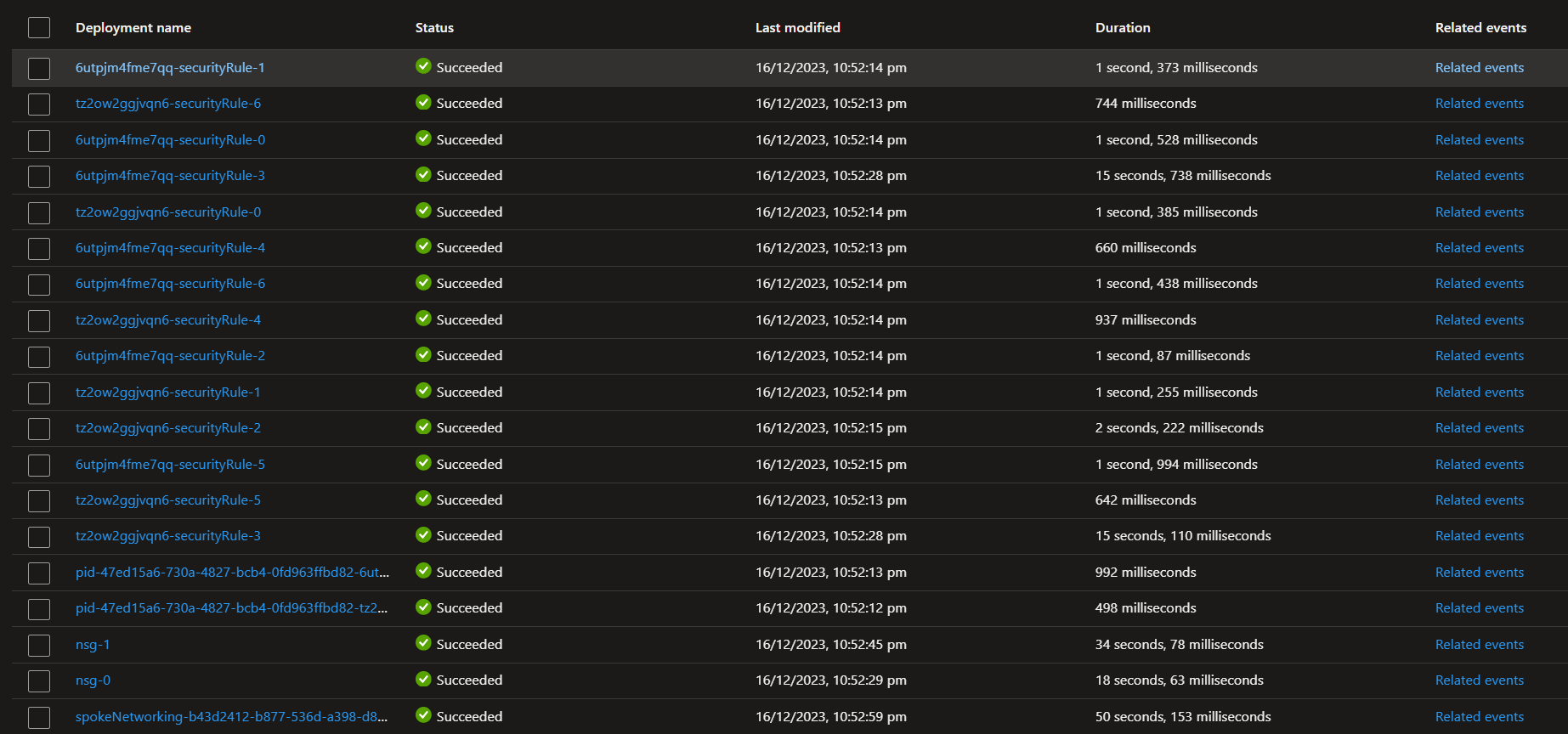
Resource Group Deployment
The network resource group deployment includes network resources, Virtual Network, Subnets, Network Security Groups and Route Tables. You will also see security rules that are within the NSG. These are defined in the shared-variables.bicep file that we discussed in Part 1 of the series.
CI/CD Deployment using GitHub Actions
We will deploy the same Landing Zone Bicep template using GitHub Actions. The GitHub Actions workflow is normally triggered when a pull request is merged into the main branch but for this we can run it on demand.
- Within the GitHub repository, navigate to the Actions tab and select the
Deploy Landing Zoneworkflow. - Click the
Run workflowbutton and select themainbranch.
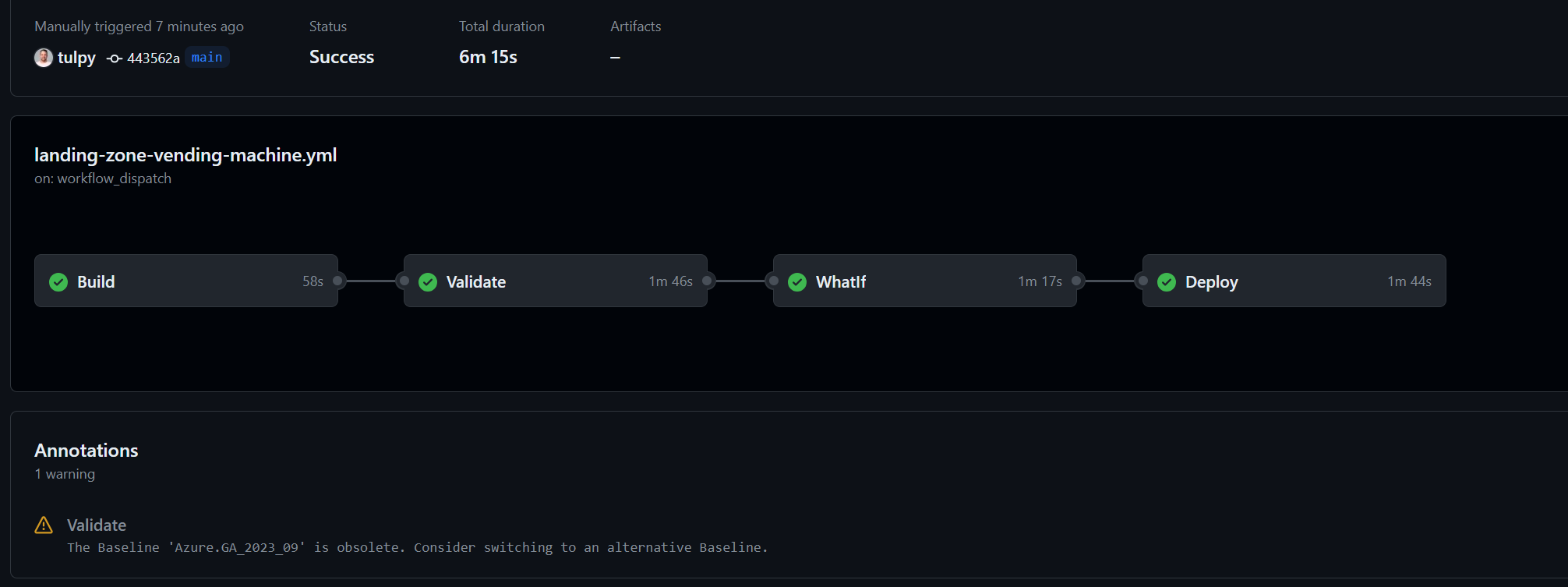
- The deployment will go through the stages as outlined in the Deploying Bicep Templates using GitHub Actions, as you can see the
Build,Validate,WhatIfandDeploystages are all successful, we also have a warning about an out of date baseline for for PSRule so we will need to update that with theAzure.GA_2023_09value.
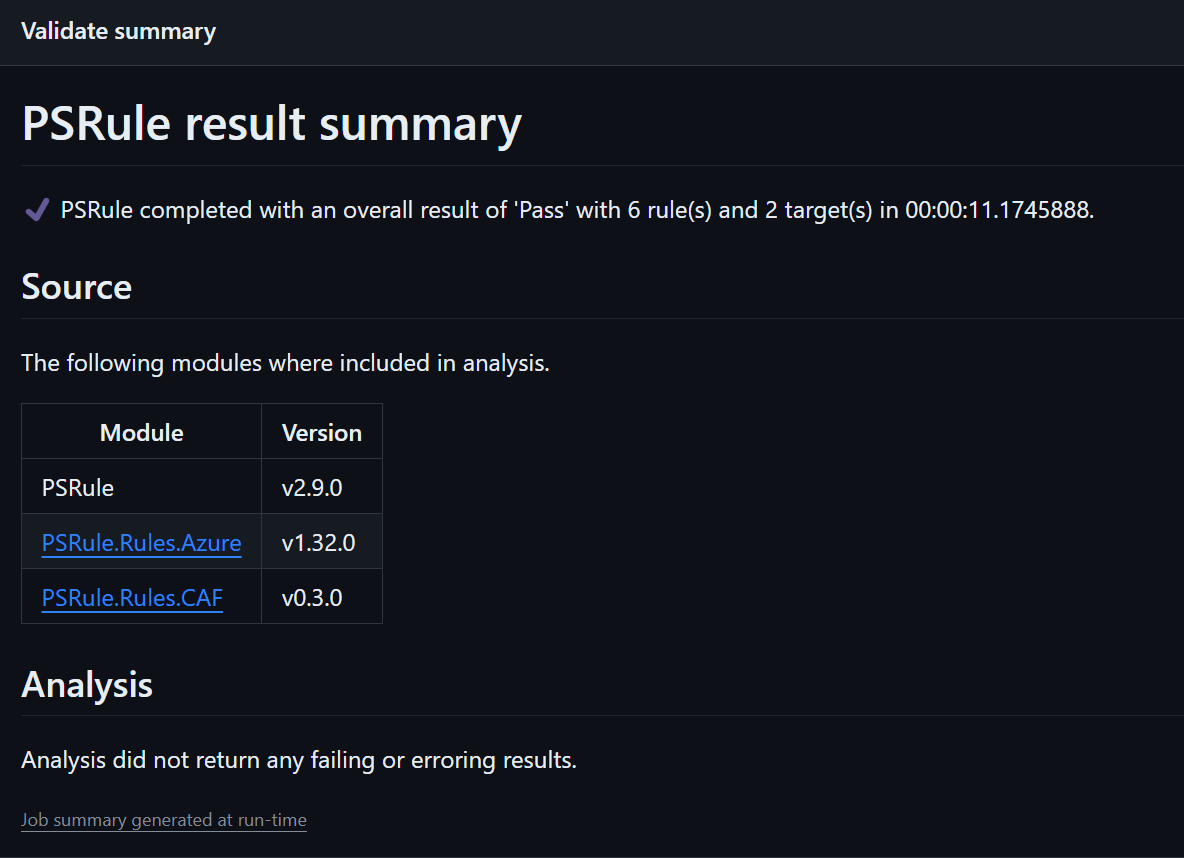
- We can also see the output of the PSRule run that gives a summary of the validation.
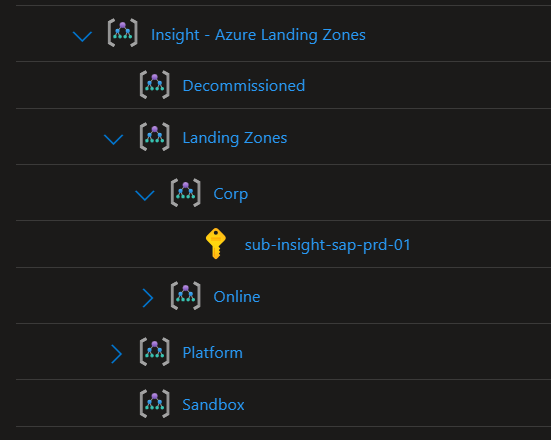
Deployed Resources within the Landing Zone
Both of the approaches to deployment will deploy the same Azure resources into the Landing Zone, lets look at each of the scoped child deployments and the resources that are deployed.
- The Landing Zone subscription is moved to the targeted Management Group as part of the deployment.
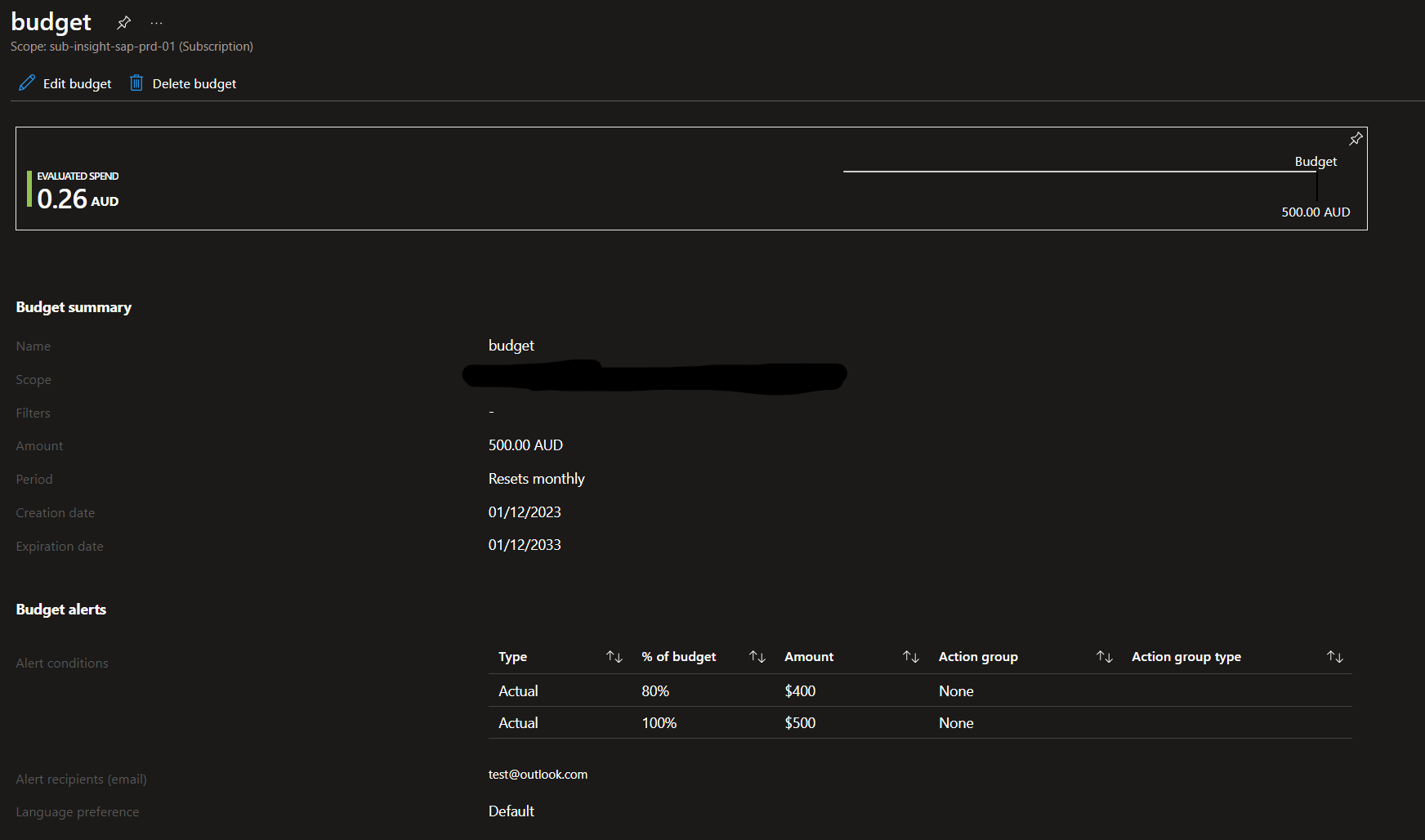
- An Azure budget is assigned to the subscription to ensure that costs are managed, with some thresholds defined
- The baseline resource groups are created in the subscription.
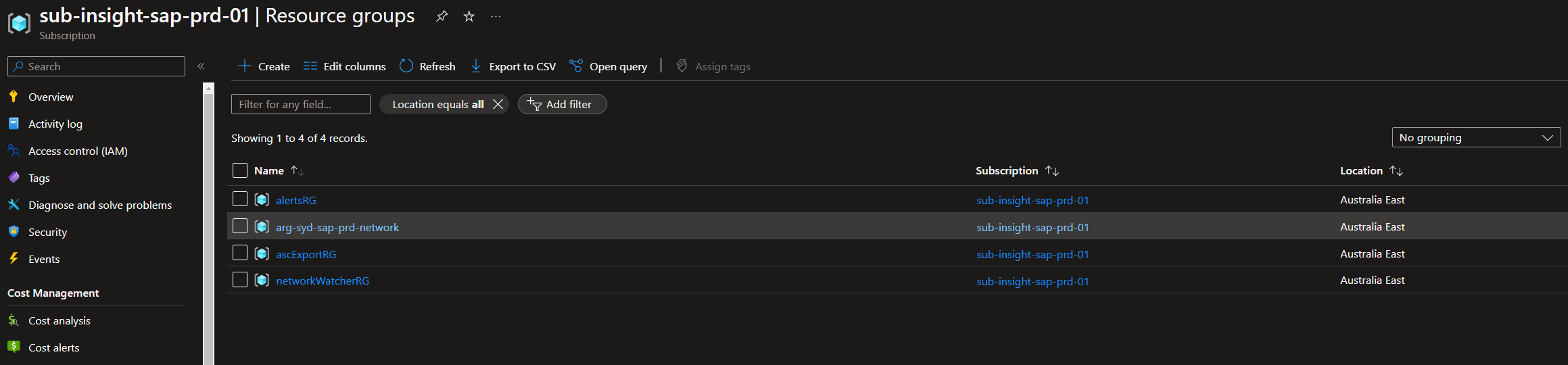
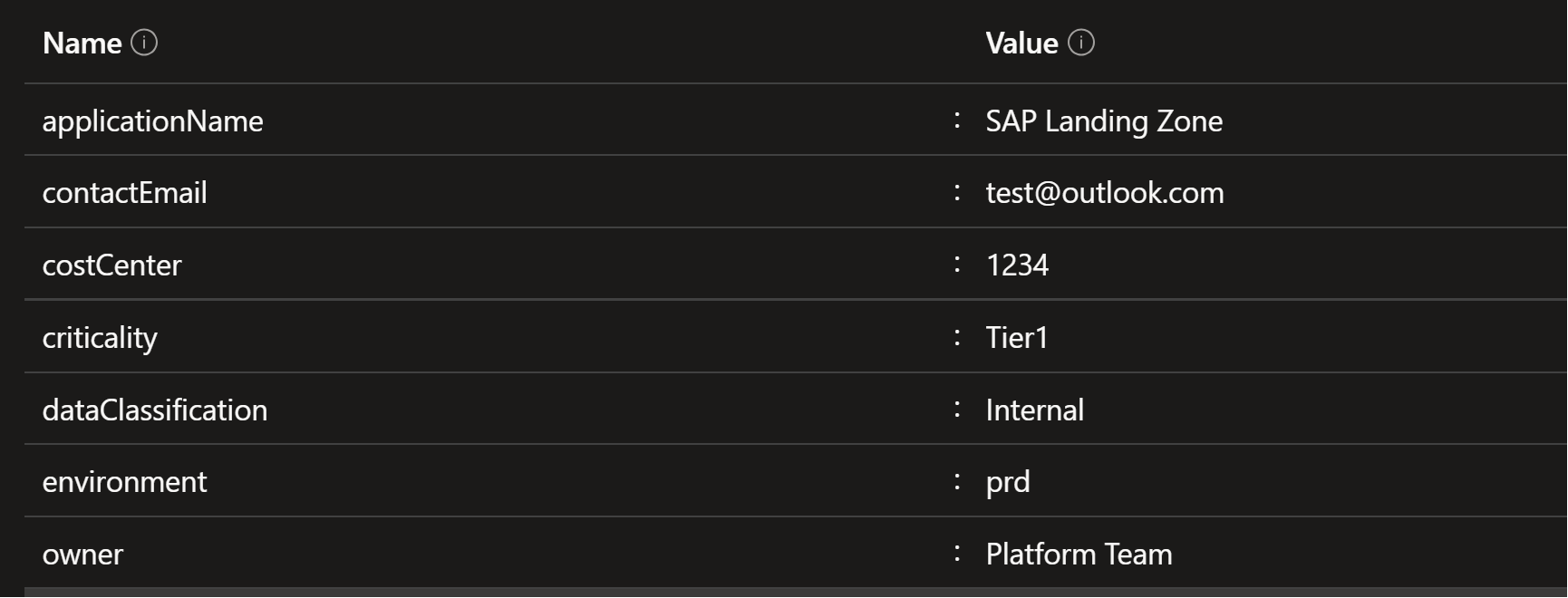
- Associated tag names and values are applied to the Subscription and Resource Groups.
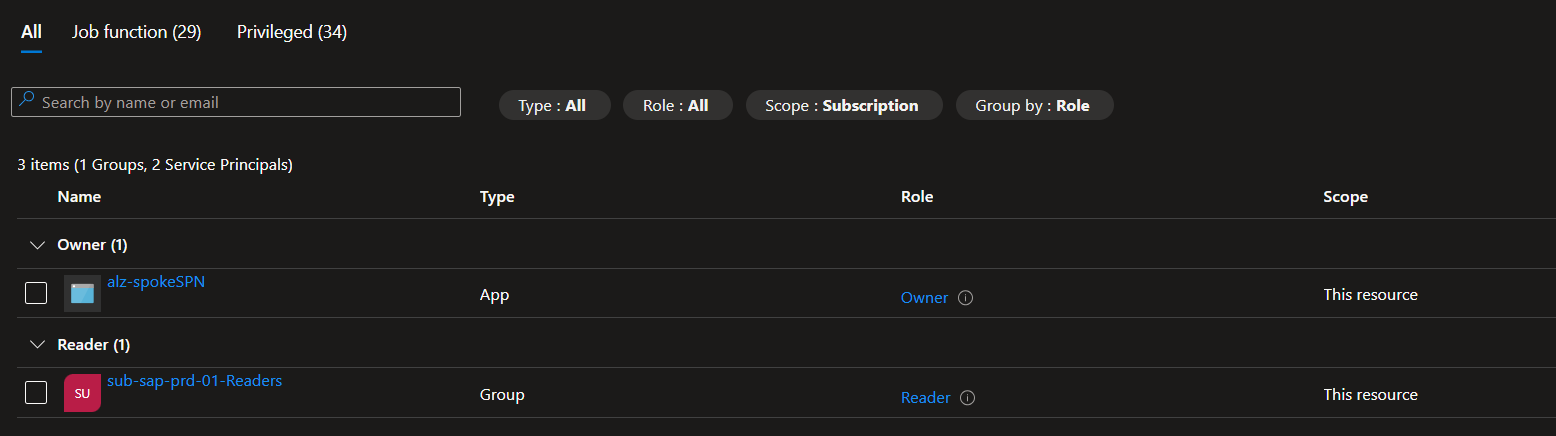
- Azure RBAC permissions for the Service Principal with Owner access and a Microsoft Entra security group for Reader access to the subscription.
- The
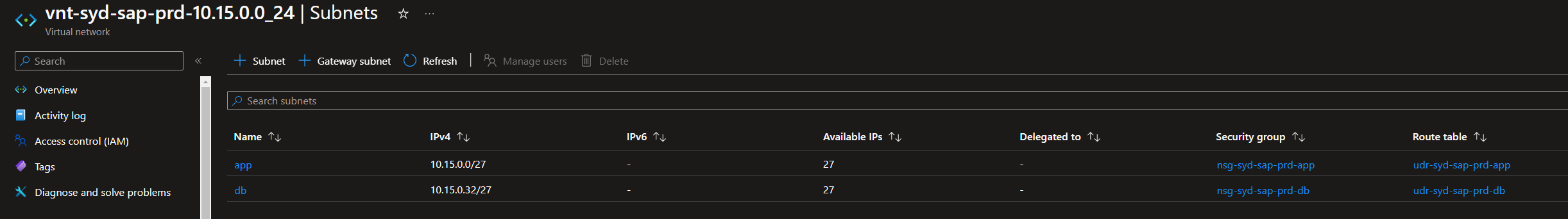
networkresource group contains all the networking resources that encompass the Landing Zone, including the Virtual Network, Subnets, Network Security Groups, Route Tables, etc.
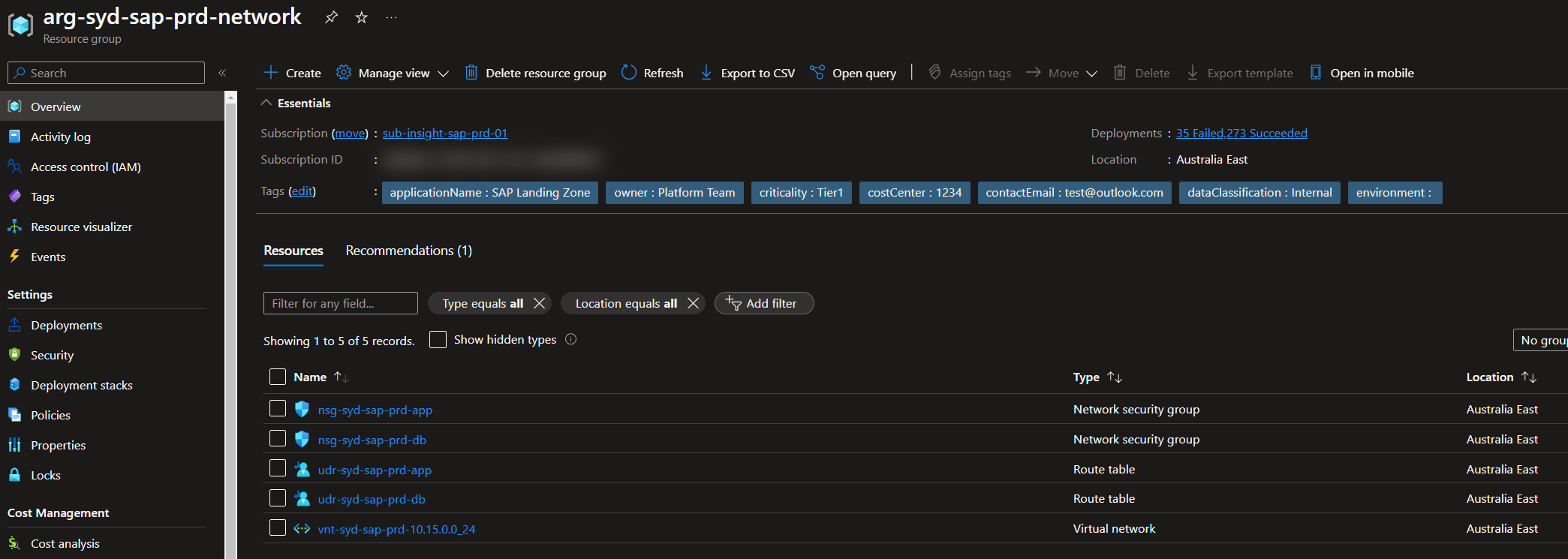
- The subnets that are defined are in the virtual network, with the associated Network Security Groups and Route Tables applied.
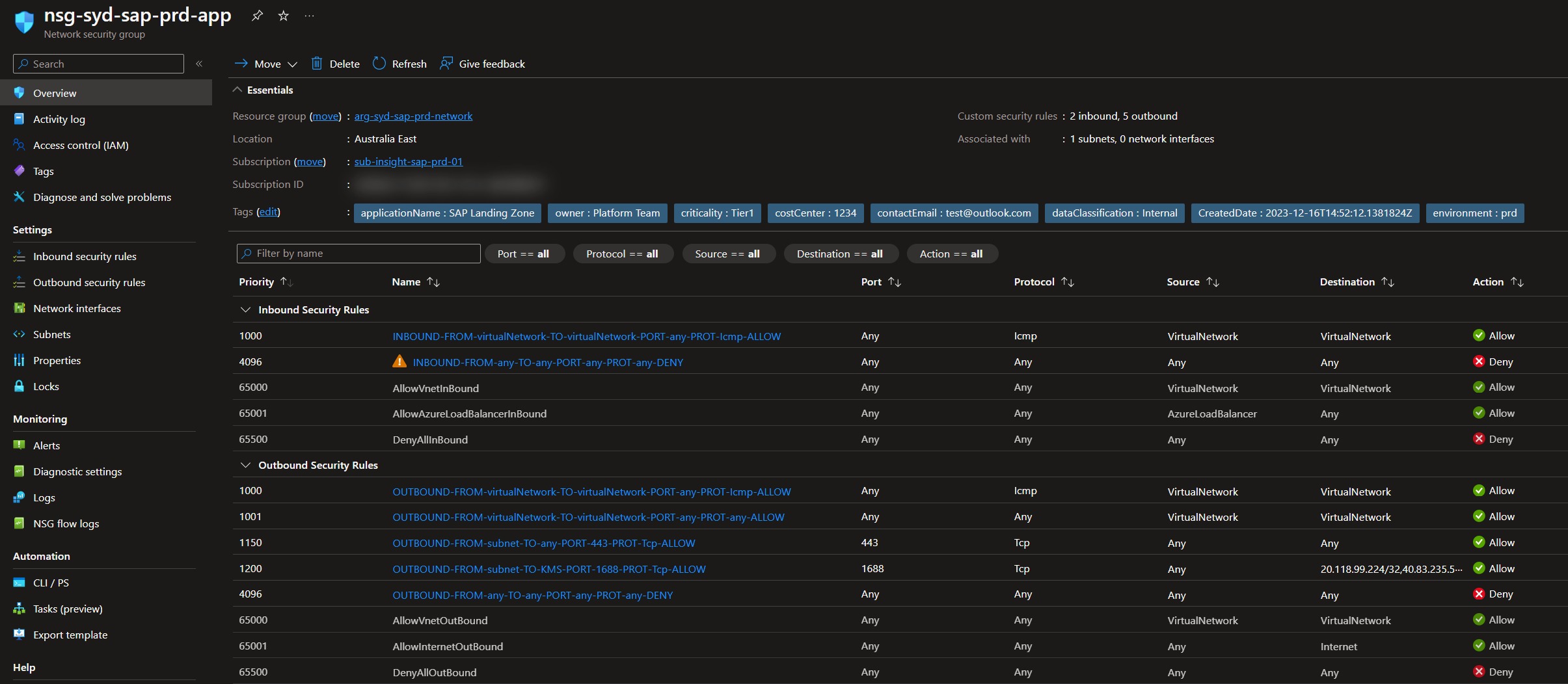
- Each of the Network Security Groups have a set of common rules that are applied using the Shared variable JSON file.
- An Action Group is created, with an email notification to the specified email address, this can be used for Subscription Owners to configure alerts for various resources.
Conclusion
Leveraging the repeatable subscription vending approach for Azure Landing Zones using Bicep, we can ensure that the Landing Zone is deployed in a secure and consistent manner within the Azure environment. Deploying locally gives us the ability to test the deployment before it is deployed into the environment and using GitHub Actions we can automate the deployment of the Landing Zone and triggers the deployment when a pull request is merged into the main branch for further changes if needed.