Enterprise Policy as Code for Security & Governance - Part 2
 Stephen Tulp
Stephen Tulp
December 20, 2024
13 minutes to read

Overview
Yesterday we learnt about the Enterprise Policy as Code (EPAC) solution for managing Azure Policy at scale using Infrastructure as Code and DevOps principles, now that we have a better understanding of the key concepts we are going to deploy this into our Azure environment.
Architecture Overview
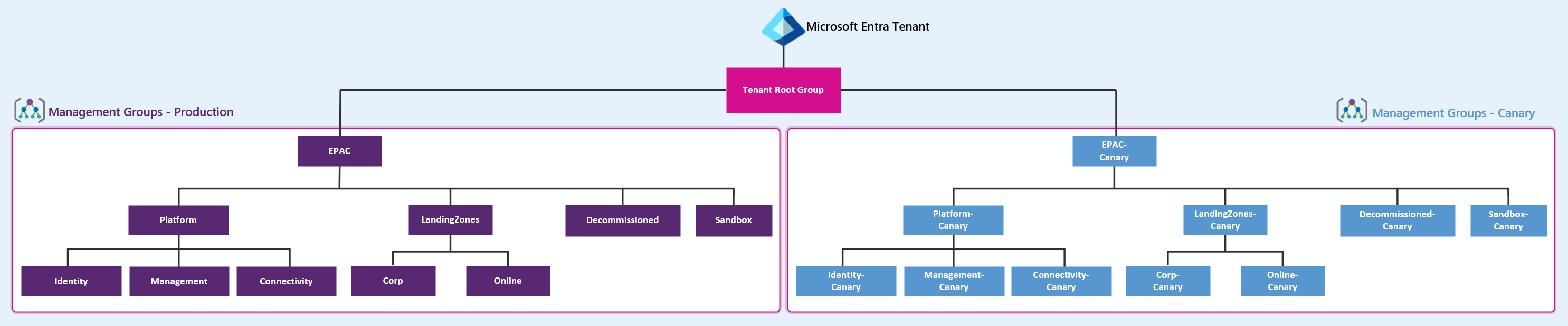
The diagram above outlines the Management Group structure that we will be using for the deployment, in yesterdays post I mentioned using a Canary approach using multiple tenants. Canary Azure landing zones environment can be used to author and test Azure Policies before you deploy them into the production environment.
The term canary is used to avoid confusion with application development environments or test environments. If you are interested in understanding more about this, then check out the Testing Approach for Azure Landing Zones
Deployment Steps
The process to bootstrap and configure the environment is straight forward
- Install the
EnterprisePolicyAsCodemodule from the PowerShell gallery and import it.
Install-Module EnterprisePolicyAsCode
Import-Module EnterprisePolicyAsCode
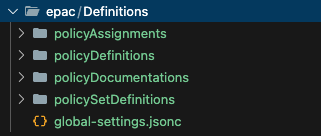
- Create a new policy definition folder structure using the command below. Your VS Code folder structure should look like the image.
New-HydrationDefinitionFolder -DefinitionsRootFolder .\Definitions
-
Update the
global-settings.jsonfile in the Definitions folder (See details below) -
Add the definitions files into the appropriate folders. There are exports for green fields environments for ALZ and AMBA Exports
-
At this point you can run the build script and generate a plan to validate what is going to be changed in the existing environment.
Build-DeploymentPlans -DefinitionsRootFolder Definitions -OutputFolder Output
- Run the generated plan to deploy the policy objects
Deploy-PolicyPlan -DefinitionsRootFolder .\Definitions -InputFolder .\Output
- Run the generated plan to update the role assignment objects
Deploy-RolesPlan -DefinitionsRootFolder .\Definitions -InputFolder .\Output
Global Settings File
We need to update the global-settings.jsonc file to reflect the Management Group structure.
{
"$schema": "https://raw.githubusercontent.com/Azure/enterprise-azure-policy-as-code/main/Schemas/global-settings-schema.json",
"pacOwnerId": "00000000-0000-0000-0000-000000000000",
"pacEnvironments": [
{
"pacSelector": "epac-canary",
"cloud": "AzureCloud",
"tenantId": "00000000-0000-0000-0000-000000000000", // Update this to your tenant Id
"deploymentRootScope": "/providers/Microsoft.Management/managementGroups/mg-epacdev", // Canary Management Group structure
"desiredState": {
"strategy": "full",
"keepDfcSecurityAssignments": false,
"doNotDisableDeprecatedPolicies": false
},
"skipResourceValidationForExemptions": false,
"managedIdentityLocation": "australiaeast"
},
{
"pacSelector": "epac-prod",
"cloud": "AzureCloud",
"tenantId": "00000000-0000-0000-0000-000000000000", // Update this to your tenant Id
"deploymentRootScope": "/providers/Microsoft.Management/managementGroups/mg-epac", // Production Management Group structure
"desiredState": {
"strategy": "full",
"keepDfcSecurityAssignments": false,
"doNotDisableDeprecatedPolicies": false
},
"skipResourceValidationForExemptions": false,
"managedIdentityLocation": "australiaeast"
}
]
}
Copy AMBA Policies into the Right Folders
For the deployment we are going to deploy the Azure Monitor Baseline Alerts project with EPAC, these policies have been extracted and converted to the EPAC format and are available in the AMBA Export repo.
There is a weekly job that syncs the policies from the upstream repo AMBA to the Export repo. The following Azure Policy Initiatives are used for the assignments.
- alerting-connectivity-policySet.jsonc
- alerting-identity-policySet.jsonc
- alerting-management-policySet.jsonc
- alerting-servicehealth-policySet.jsonc
- notification-assets-policySet.jsonc
Adjust the following fields in the assignment files to suit the MG structure and required settings.
- scope
- managedIdentityLocations
- parameters
Build Policy & Role Plans for EPAC-Canary
We are going to build the Policy & Role Plans to get an understanding of what will be deployed into the environment.\, choosing epac-canary as the environment.
Build-DeploymentPlans -DefinitionsRootFolder Definitions -OutputFolder Output
The script will run through the environment looking at Management Groups, Subscriptions and Resource Groups. It will also pick up Policy Definitions, Policy Initiatives, Policy Assignments and Role Assignments. We can see the summary of the plan and the New, Updated, Replaced, or Deleted resources.
===================================================================================================
Summary
===================================================================================================
Policy counts:
0 unchanged
116 changes:
new = 116
update = 0
replace = 0
delete = 0
Policy Set counts:
0 unchanged
14 changes:
new = 14
update = 0
replace = 0
delete = 0
Policy Assignment counts:
0 unchanged
15 changes:
new = 15
update = 0
replace = 0
delete = 0
Role Assignment counts:
15 changes:
add = 15
update = 0
remove = 0
---------------------------------------------------------------------------------------------------
Output plan(s); if any, will be written to the following file(s):
Policy resource deployment required; writing Policy plan file 'Output/plans-epac-canary/policy-plan.json'
Role assignment changes required; writing Policy plan file 'Output/plans-epac-canary/roles-plan.json'
---------------------------------------------------------------------------------------------------
The policy-plan.json and roles-plan.json files are located in Outputs/plans-epac-canary folder.
Deploy Policy & Role Plans for EPAC-Canary
Deploying the policy-plan.json and roles-plan.json will create the associated Azure Policy Definitions, Initiatives and Assignments
Deploy-PolicyPlan -DefinitionsRootFolder .\Definitions -InputFolder .\Output
We can see the information that is pulled from the global-settings.jsonc
===================================================================================================
Read global settings from '.\Definitions/global-settings.jsonc'.
===================================================================================================
PowerShell Versions: 7.4.0
PAC Environments: epac-canary, epac-prod
PAC Owner Id: 00000000-0000-0000-0000-000000000000
Definitions root folder: .\Definitions
Input folder: .\Output
Output folder: Output
Select Policy as Code environment [epac-canary, epac-prod]: epac-canary
Environment Selected: epac-canary
cloud = AzureCloud
tenant = 00000000-0000-0000-0000-000000000000 // redacted
root scope = /providers/Microsoft.Management/managementGroups/mg-epacdev
Telemetry is enabled
***************************************************************************************************
Deploy Policy resources from plan in file '.\Output/plans-epac-canary/policy-plan.json'
Plan created on 2024-12-20 03:26:52Z.
***************************************************************************************************
Then it goes through with the deployment.
===================================================================================================
Create and update Policies (116) // Truncated for screenshots
---------------------------------------------------------------------------------------------------
Deploy PDNSZ Capacity Utilization Alert
Deploy Activity Log Azure FireWall Delete Alert
Deploy App Service Plan Disk Queue Length Alert
Deploy PIP Bytes in DDoS Attack Alert
Deploy Activity Log LA Workspace Delete Alert
Deploy PDNSZ Record Set Capacity Alert
Deploy ERG ExpressRoute CPU Utilization Alert
Deploy VM CPU Alert
Deploy VM Memory Alert
Deploy AGW CPU Utilization Alert
Deploy VM HeartBeat Alert
Deploy Activity Log Storage Account Delete Alert
Deploy ERG ExpressRoute Bits In Alert
Deploy ExpressRoute Circuits QosDropBitsOutPerSecond Alert
Deploy Resource Health Unhealthy Alert
Deploy AGW FailedRequests Alert
Deploy VM Network Write Alert
Deploy ER Direct ExpressRoute TxLightLevel Low Alert
Deploy FrontDoor CDN Profile Origin Latency Alert
Deploy Hybrid VM HeartBeat Alert
Deploy Hybrid VM OS Disk Space Alert
===================================================================================================
Create and update Policy Sets (14)
---------------------------------------------------------------------------------------------------
Deploy Azure Monitor Baseline Alerts for Key Management
Deploy Azure Monitor Baseline Alerts for Service Health
Deploy Azure Monitor Baseline Alerts for Management
Deploy Azure Monitor Baseline Alerts for Web
[Deprecated]: Deploy Azure Monitor Baseline Alerts for Landing Zone
Deploy Azure Monitor Baseline Alerts for Load Balancing
Deploy Azure Monitor Baseline Alerts for Recovery Services
Deploy Azure Monitor Baseline Alerts for Storage
Deploy Azure Monitor Baseline Alerts for Virtual Machines
Deploy Azure Monitor Baseline Alerts for Identity
Deploy Azure Monitor Baseline Alerts for Hybrid VMs
Deploy Azure Monitor Baseline Alerts for Connectivity
Deploy Azure Monitor Baseline Alerts - Notification Assets
Deploy Azure Monitor Baseline Alerts for Changes in Network Routing and Security
===================================================================================================
Create and update Assignments (15)
---------------------------------------------------------------------------------------------------
Deploy Azure Monitor Baseline Alerts for Management - /providers/Microsoft.Management/managementGroups/mg-epacdev-platform-management/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-Management
Deploy Azure Monitor Baseline Alerts for Service Health - /providers/Microsoft.Management/managementGroups/mg-epacdev/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-SvcHealth
Deploy Azure Monitor Baseline Alerts for Storage - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-Storage
Deploy Azure Monitor Baseline Alerts for Virtual Machines - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-VM
Deploy Azure Monitor Baseline Alerts for Hybrid VMs - /providers/Microsoft.Management/managementGroups/mg-epacdev-platform/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-HybridVM
Deploy Azure Monitor Baseline Alerts for Web - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-Web
Deploy Azure Monitor Baseline Alerts for Key Management - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-KeyMgmt
Deploy Azure Monitor Baseline Alerts for Identity - /providers/Microsoft.Management/managementGroups/mg-epacdev-platform-identity/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-Identity
Deploy Azure Monitor Baseline Alerts for Recovery Services - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-RecoverySvc
Deploy Azure Monitor Baseline Alerts for Virtual Machines - /providers/Microsoft.Management/managementGroups/mg-epacdev-platform/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-VM
Deploy Azure Monitor Baseline Alerts - Notification Assets - /providers/Microsoft.Management/managementGroups/mg-epacdev/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-Notification
Deploy Azure Monitor Baseline Alerts for Connectivity - /providers/Microsoft.Management/managementGroups/mg-epacdev-platform-connectivity/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-Connectivity
Deploy Azure Monitor Baseline Alerts for Hybrid VMs - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-HybridVM
Deploy Azure Monitor Baseline Alerts for Changes in Network Routing and Security - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-NetworkChang
Deploy Azure Monitor Baseline Alerts for Load Balancing - /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones/providers/Microsoft.Authorization/policyAssignments/Deploy-AMBA-LoadBalance
- Run the generated plan to update the role assignment objects
Now to complement the Azure Policy Assignments we need to run Role Assignments.
Deploy-RolesPlan -DefinitionsRootFolder .\Definitions -InputFolder .\Output
System Identities will be created for each Policy Assignment that has a DeployIfNotExist effect on it.
***************************************************************************************************
Deploy Role assignments from plan in file '.\Output/plans-epac-canary/roles-plan.json'
Plan created on 2024-12-20 03:26:52Z.
***************************************************************************************************
===================================================================================================
Add (15) new Role assignments
---------------------------------------------------------------------------------------------------
Assignment 'Deploy Azure Monitor Baseline Alerts for Connectivity', principalId 6ab1463a-187b-45fc-990d-727252cb9066, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-platform-connectivity
Assignment 'Deploy Azure Monitor Baseline Alerts for Hybrid VMs', principalId 4568126b-2481-4f04-a825-dc004cbec317, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-platform
Assignment 'Deploy Azure Monitor Baseline Alerts for Hybrid VMs', principalId 9cce6bcb-261e-47df-a836-4e7df9c3a2b9, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts for Identity', principalId 61ab564d-d627-4487-8d0f-e49b7e44f98d, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-platform-identity
Assignment 'Deploy Azure Monitor Baseline Alerts for Key Management', principalId dad3672c-de34-4182-ada7-6d3a3f2a2ced, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts for Load Balancing', principalId 5dd45474-b6c3-45ea-9956-1f2629bb2563, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts for Management', principalId 209b465e-0fc9-45ef-8f12-c6b30ad4ed16, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-platform-management
Assignment 'Deploy Azure Monitor Baseline Alerts for Changes in Network Routing and Security', principalId f78356da-0fd6-447f-b7fe-f4565c8bcfdc, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts for Recovery Services', principalId 9c08e0ac-e3cb-48e5-adc5-c158e60a08d2, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts for Service Health', principalId 98bf7e88-65f2-4551-ae23-b713bbf54a15, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev
Assignment 'Deploy Azure Monitor Baseline Alerts for Storage', principalId de83aadd-0247-4881-876d-4e9d5d79c11b, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts for Virtual Machines', principalId 25bba9e2-78d3-4a61-bfec-233a8337928a, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-platform
Assignment 'Deploy Azure Monitor Baseline Alerts for Virtual Machines', principalId b68b65b7-d15f-46b9-9c07-6418c6338156, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts for Web', principalId 0294751e-551f-46e4-b522-e79b2956606d, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev-landingzones
Assignment 'Deploy Azure Monitor Baseline Alerts - Notification Assets', principalId 0c3851e0-8bd2-4b30-b21c-045f7b5ab87f, role 'Contributor' at /providers/Microsoft.Management/managementGroups/mg-epacdev
EPAC-Prod
Once the EPAC-Canary deployment is complete, the level of validation and testing is up to your governance processes and what you need to do to feel comfortable with deploying to production. The process is the same for the Production tenant you need to pick that one as part of the deployment.
Conclusion
We have only scratched the surface to what is possible, we can now setup CI/CD pipelines to automate this end to end to cover the same scenario above. If we are using a brown fields environment that already has policies deployed but they aren’t in IaC we can also run the Export-AzPolicyResources command to extract
existing Policies, Policy Sets, and Policy Assignments and Exemptions outputting them in EPAC format into sub-folders in folder $outputFolders/Definitions. The sub-folders are policyDefinitions, policySetDefinitions, policyAssignments and policyExemptions.
You can also start creating your own policies to follow, more details below.